 Contact us
Contact us
Our commitment is to ensure users globally enjoy unbreakable Cloud Storage Security. With Got Backup Encryption, safeguard your most sensitive data, including private documents, photos, and videos, across all your devices. Rest assured, not even Got Backup administrators can access your content. Your online privacy remains solely in your control.
Zero-knowledge privacy
Implementing zero-knowledge privacy ensures that neither we, as the service provider, nor any external authority or entity will ever gain access to your data. Our encryption employs multiple layers of protection and keys. Furthermore, users secure their files and account with a password generated solely by them, rendering them invisible to unauthorized parties. We simply encrypt everything - to know nothing.
Since the enactment of the General Data Protection Regulation (GDPR) in the EU in May 2018, which has influenced global legislative trends, there has been an intensified emphasis on the safeguarding of personal information. This directive, along with various international statutes, mandates that all entities managing personal data employ cutting-edge safeguards. A failure to secure personal data against unauthorized exposure could result in legal, financial, or brand damage. Data confidentiality, however, is the act of protecting any sensitive information crucial to a company or individuals, often mandated by legal agreements like NDAs to maintain strict internal control over corporate information. Under GDPR, data protection is achievable through physical and administrative strategies. The former prevents unsanctioned access to your data infrastructure, while the latter ensures that all administrative activities are documented and traceable. These measures typically suffice for GDPR compliance.
Encryption is a three-tiered safeguard in GotBackup's arsenal for ensuring data protection and confidentiality. Encryption can be obligatory, advantageous, or burdensome, and within GotBackup's environment, it occurs at three stages: during transmission, while stored, and at the user endpoint, with the latter also known as end-to-end encryption.
In-Transit Encryption: GotBackup inherently secures data in transit using HTTPS and the latest TLS protocols across all compatible browsers and clients, as well as for all server connections. GDPR mandates this level of encryption, and it's a standard recognized by legal precedent for maintaining data confidentiality.
2a. At-Rest Encryption: GotBackup secures files on the server before storing them by using a master key encryption method compatible with all storage systems. S3 object storage users should use the native encryption feature. This method is designed to prevent data access from storage devices, including in cases of theft.
2b. At-Rest Encryption with HSM: To prevent system administrators from decrypting files, GotBackup allows for master keys to be stored within a Hardware Security Module (HSM). File keys are processed within the HSM, inaccessible to administrators as long as the server remains secure. HSMs are available in various formats, including as software and USB devices, and GotBackup supports those compliant with PKCS 11 standards.
End-to-End Encryption: This is the most secure form, ensuring that encrypted data is inaccessible to unauthorized parties, including system administrators. However, users must balance the need for confidentiality with performance impacts. It allows users to encrypt folders and manage file sharing securely within the browser, without storing private keys within the browser, thereby offering enhanced security.
In conclusion, GotBackup's various encryption methods, from in-transit to end-to-end, provide comprehensive data protection and secrecy capabilities, tailored to meet the stringent requirements of global data protection regulations.

Data at rest and in transit is always encrypted at Got Backup for all data and all data cloud migrations. Any data in motion is highly vulnerable to threats since it is exposed directly to the internet. Therefore we use a secure transport protocol like Hypertext Transfer Protocol Secure (HTTPS) which eliminates the vulnerability of having your data compromised.
HTTPS appears in the URL when a website is secured by an SSL/TLS certificate. SSL is the abbreviation for secure sockets layer which enables authentication of the server to the user and encryption of data transferred between the server and the user. SSL secure sockets layer prevents hackers from seeing or stealing any information transferred, including personal or financial data. It also prevents attackers from tampering with data in transit, like a tamper-proof seal on a medicine container.
Got Backup is obsessed with these multiple layers of security including having AES 256-bit encryption everywhere.
How Does 256-Bit Encryption Work?
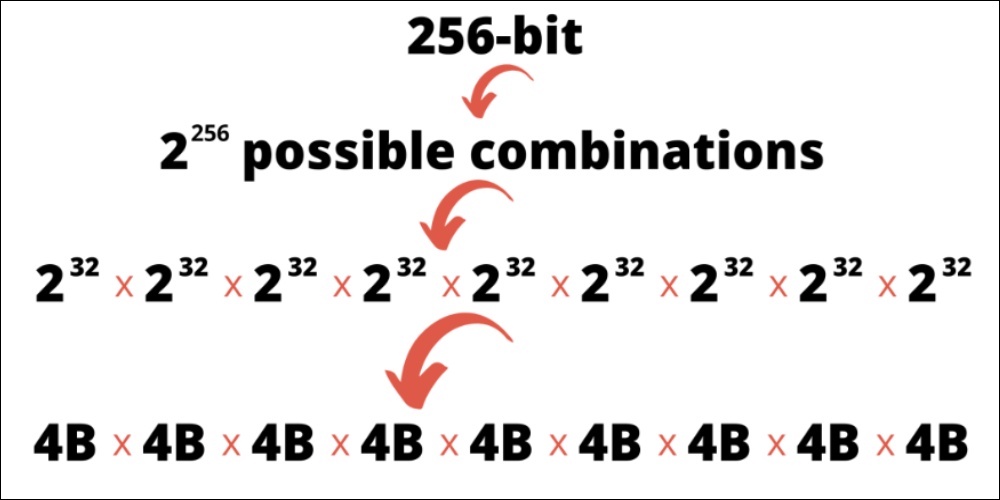
256-bit encryption works by locking data or a file using a secret key that is 256-bit long. Now, it may be difficult to imagine how long that key is, so let’s convert it into a more relatable number. How many possible combinations are there if you need to guess what the 256-bit long secret key is?
You have 2256 possibilities, which are equivalent to 232 multiplied by itself eight times. To visualize this number more, we can convert 232 to its equivalent, which is 4,294,967,296. Therefore, the number of possible secret key combinations when using 256-bit encryption is 4 billion multiplied by itself eight times.
Can You Break 256-Bit Encryption?
With an infinite number of possible combinations, can anyone break 256-bit encryption? Hackers are known to use brute force, which involves guessing the password until the correct combination is submitted.
To put things into perspective, consider an email account with a password consisting of eight alphanumeric characters. Password Depot estimates that there are about 457 trillion possible combinations, and it would take hackers 2.6 days to decrypt it through brute force. A 12- character password, on the other hand, is a different story. Decryption would take approximately 7.5 million years.
Several experts concluded that it is impossible to break 256-bit encryption even if people use the most powerful computer.
